AI Remediations
AI Remediations in Nirmata Control Hub (NCH) enable automated, context-aware suggestions for resolving policy violations in your workloads and resources. This feature is designed to accelerate remediation workflows while improving compliance and security posture across your environments.
NOTE: AI Remediations are currently available in preview mode. Please contact your customer success representative to enable this feature for your account.
Prerequisites
- Remediation Assistant should be enabled for your tenant.
- Go to Settings>AI and enable Remediation Assistant.
NOTE: Only users with Admin access can change the AI settings for the tenant.
How it Works
When a workload or resource in your cluster violates policies or rules defined in NCH, the system can now generate AI-powered remediation suggestions. These are based on the specific context of the resource and the policy violation.
Key details:
- Remediations are generated using Cloud 3.7, a large language model (LLM).
- The suggestions are designed to provide a first-level fix to bring resources back into compliance.
- Each remediation includes a summary of the changes and a rationale for the suggested fix.
NOTE: While AI-generated remediations are often accurate and actionable, it is strongly recommended to review and test all changes before applying them to production or target environments.
Supported Resources
AI Remediations can be generated for any Kubernetes resource that violates policy—this includes Deployments, Services, ConfigMaps, NetworkPolicies, and more.
Viewing Remediation Suggestions in NCH
- Go to Policy Reports>Namespace>Resources.
- For every resource with one or more violations, the
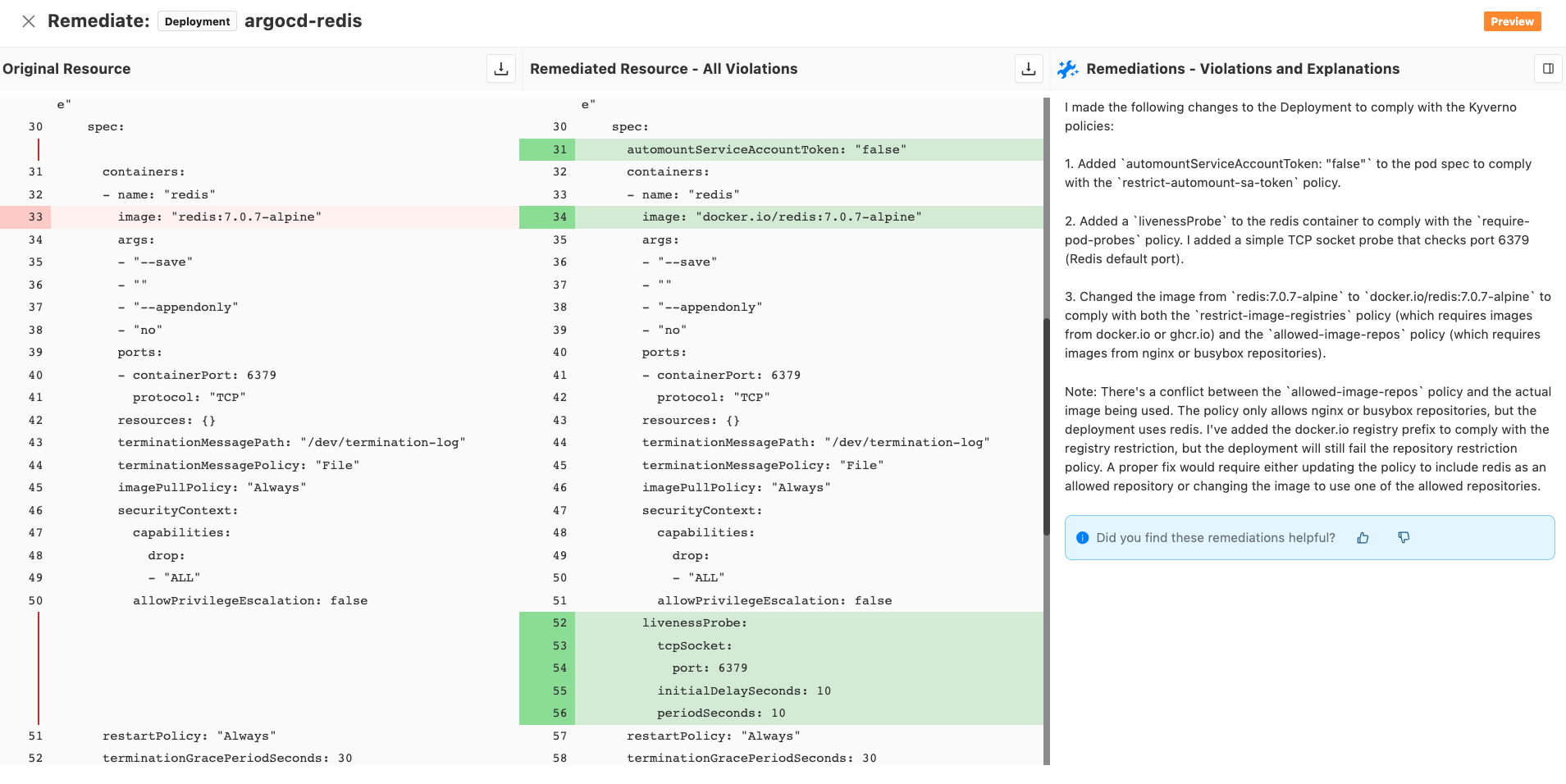
Actionscolumn has a remediate option. - Clicking on the remediate icon will show a diff of actual resource vs the remediated resource.
- Review the changes suggested and also go through the explanation to understand why a particular change is necessary.
Best Practices
- Always validate AI-generated remediations in a test environment before promoting to production.
- Treat AI Remediations as guided suggestions - ideal for improving MTTR (Mean Time to Remediate) and accelerating developer feedback loops.
- Integrate with your GitOps or CI pipelines for automated yet controlled rollouts.
