Compliance
Kyverno policies map to one or more compliance controls and compliance standards. Policy violations are generated when a resource fails a policy rule. A compliance standard contains various controls or rules that policies need to comply with.
To view the Compliance report:
- Go to Menu>Compliance. The Compliance Standards page with the default standards is displayed. In the top right corner of each standard, click the Kebab Menu to view the options: Details, Generate Report, Clone, Disable, and Delete. Additionally, the Edit option is displayed for User Managed Standards. Select any option for the respective action.
- Click any default standard, for example, CIS Benchmarks v8. The CIS Benchmarks v8 report will be displayed.
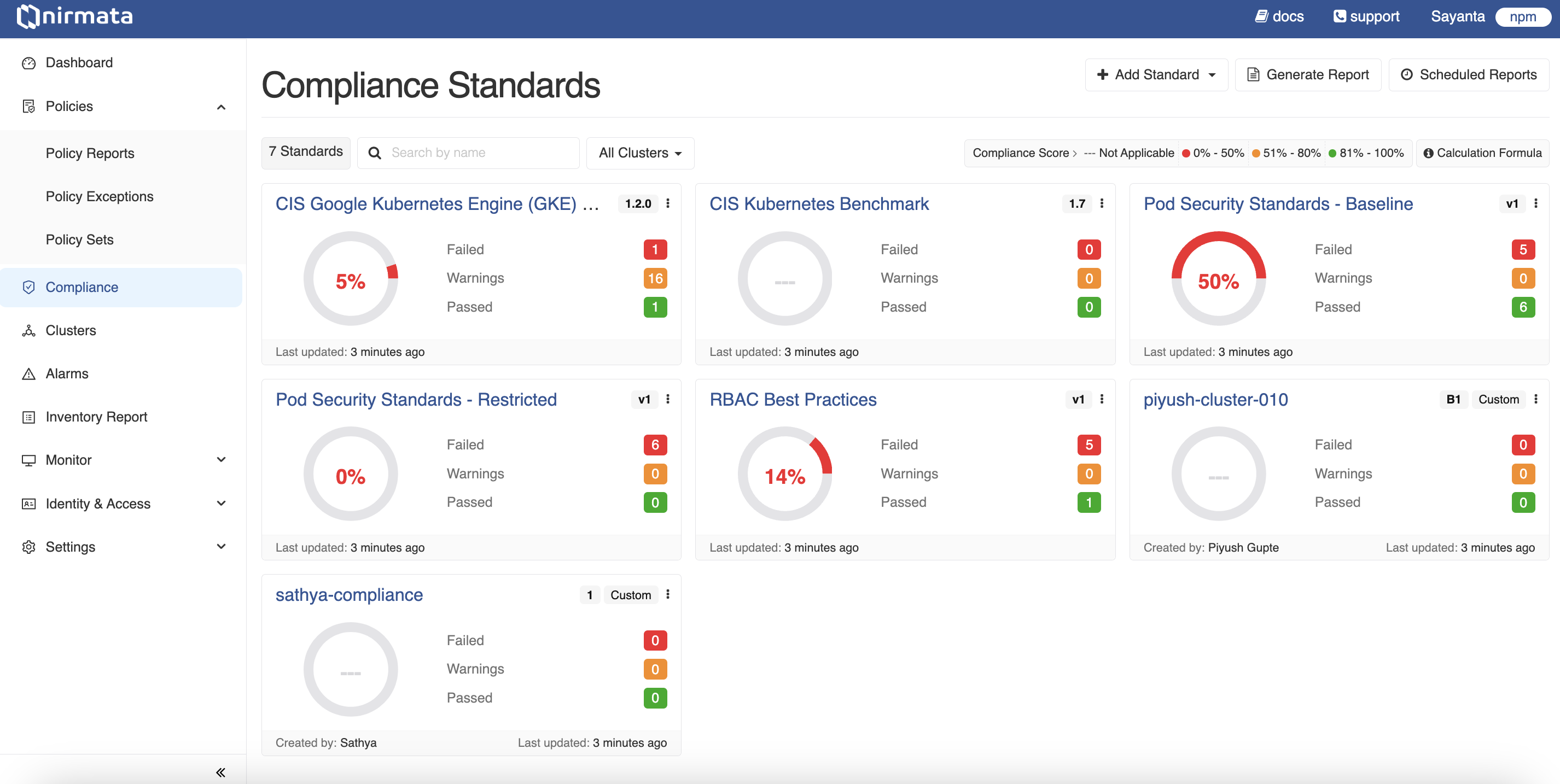
By default, the report shows Controls. Click the Clusters button to view the report for clusters. You can view the report for All Clusters or search for a particular cluster in the Search field. Additionally, you can filter by status and view the report for a particular status such as pass.
-
Click on the control name to see the details of the control, its status, policy mappings, and findings. Similarly by clicking on the Clusters button, you can view the cluster list and clicking on the cluster name, you can view the controls associated with it. You can also click on the control name to see the details of the control.
-
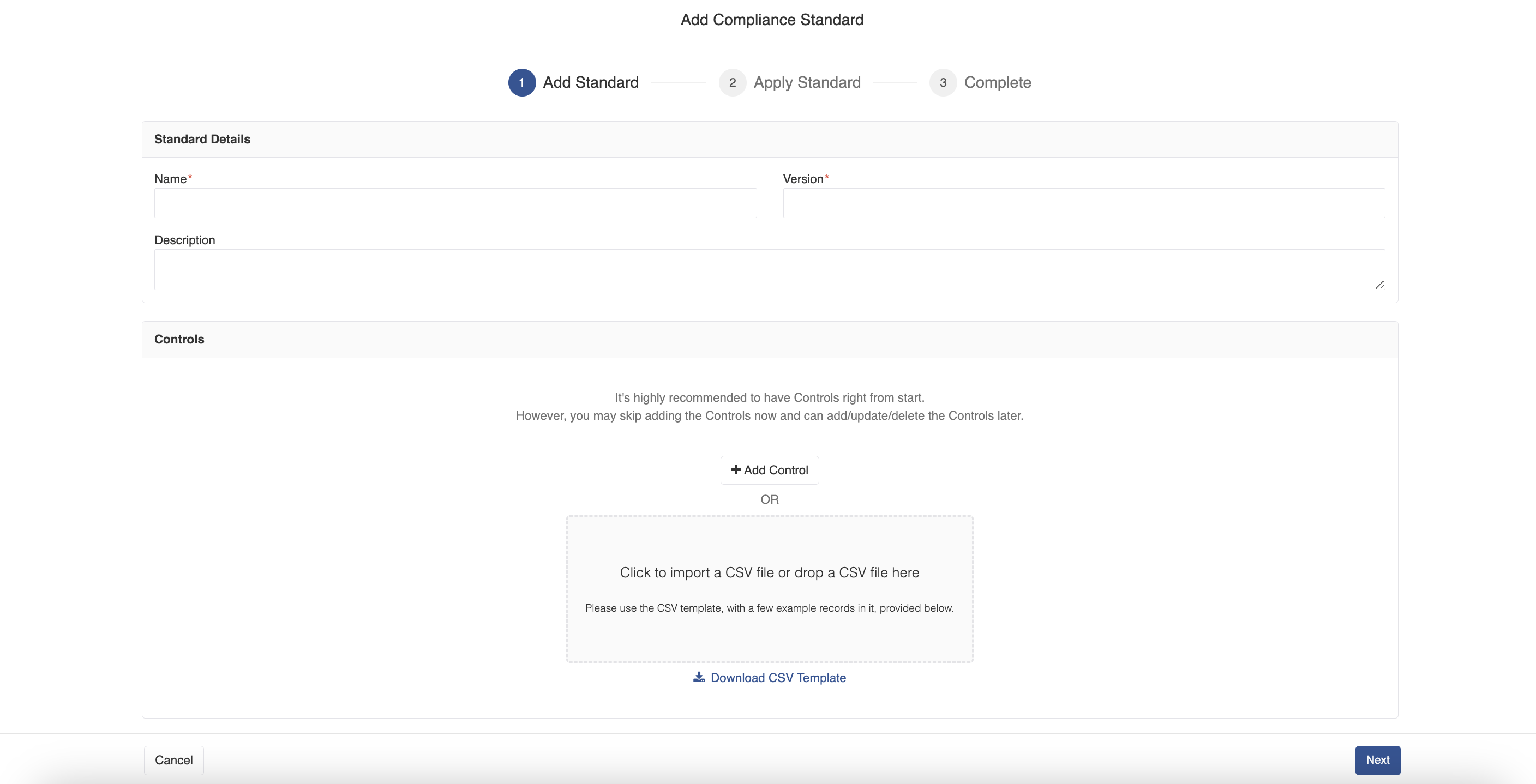
In the Compliance Standards page, click the Add Standard button to add a standard. A drop-down list of Nirmata Managed Standards and an option to add User Managed Standard are displayed. When you click the Nirmata Managed option, it is directly added. When you click the User Managed option, the Add Compliance Standard window opens.
a. Enter Name, Version and Description and click Save.
b. In the Controls block, you can either add a control by clicking on the Add Control button or import a CSV file by clicking the block, Click to import a CSV file or drop a CSV file here.NOTE: Nirmata recommends you to add controls while adding the standard. However, you can skip this step and can add/update/delete controls later.
c. Click on the Download CSV Template link to download the example template.
d. When you click on the Add Control button, the Add Compliance Control window opens. On this window, add Control Details such as Name, ID, SubID, Description, select Cloud Providers such as EKS, AKS, GKE, or Self Managed, and add Policy Mappings such as Policy Name, Rule, UUID, and click Save.
-
Click on the Generate Report button to generate a report on the standard. The Generate Report page opens.
a. In the Mail block, enter Sender, Recipients, Subject, Message details.
b. Select the Schedule checkbox to schedule the email. The options available are hourly, daily, weekly, and monthly.
c. Click on the Save button. -
Click on the Scheduled Reports and click on the + symbol to schedule a periodic email to notify any policy violations. The Schedule Email window opens.
a. Select a cluster from the list or search the cluster and click Next. The Schedule Email page is displayed.
b. In the Scope block, select the radio button, either Cluster or Namespaces to choose the scope of the report.
c. In the Mail block, enter Sender, Recipients, Subject, Message details.
d. Select the Schedule checkbox to schedule the email. The options available are hourly, daily, weekly, and monthly.
e. Click on the Save button. -
Go to Policies>Policy Reports. Click on the Kebab Menu at the right corner of the screen. The Enable CIS Benchmarks option is displayed.
-
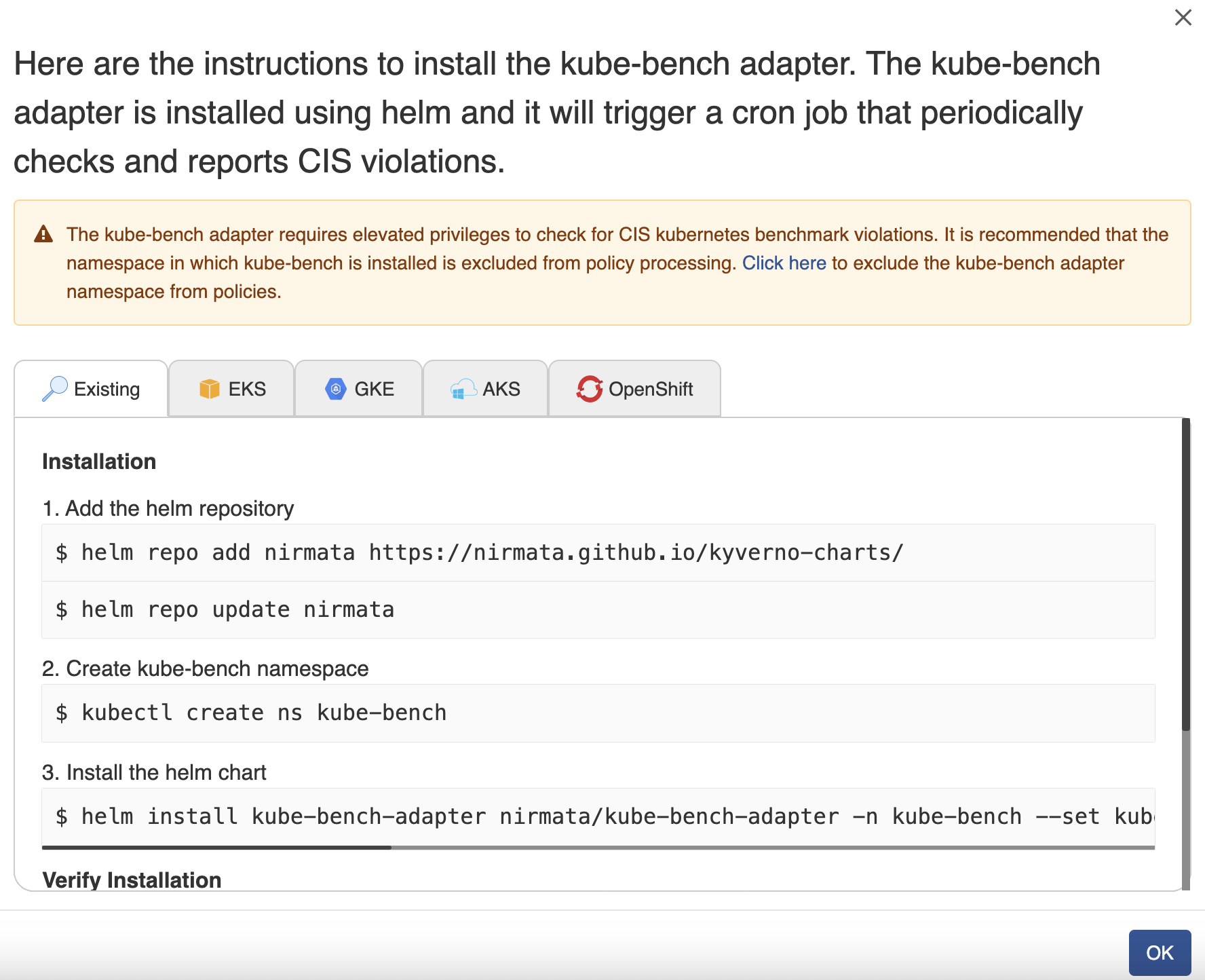
Click on the Enable CIS Benchmarks option. A window to install kube-bench adapter is displayed. In this window you will see the instructions to execute commands to install the helm chart and run the cron job to see policy violations immediately.
NOTE: Installing kube-bench adapter prompts the user to check policy reports and report CIS Benchmark violations on a weekly schedule.
- Click OK.